This article is more than 1 year old
It's all very well hacking ISIS, Barry, but what about your ISA?
HPE has a look at the business of hacking
Credit card fraud is in decline while ad fraud is poised for growth, according to a new study on the business of cybercrime out Tuesday.
Hewlett Packard Enterprise’s (HPE) study provides a detailed look into the inner workings of cybercriminal organisations, their business functions, motivations, and more. The IT giant posits that hacking groups have come to resemble legitimate technology enterprises, and attackers have become almost corporate in their behaviour.
“Their business looks a lot like ours. Cyber criminals look to maximise their profits and minimise risk,” HPE argues. “They have to compete on quality, customer service, price, reputation, and innovation. The suppliers specialise in their market offerings. They have software development life-cycles and are rapidly moving to Software as a Service (SaaS) offerings. Our businesses overlap in so many ways that we should start to look at these attackers as competitors.”
HPE’s report explores hacking as a business, diving into the different ways people make money through hacking, their motivations, value chain and organisational models.
Credit card fraud - long the main staple of underground marketplaces - is in decline because of innovations such as Chip and PIN that make card forgery more difficult. However there is still money to be made and mobile might provide a rebound in payment fraud, according to HPE’s researchers.
While there is still big money to be made in credit card fraud, the market is flooded and the business is in the declining phase. The introduction of EMV chip and PIN cards in the United States will make it harder for attackers to make money on “card‐present” transaction fraud. Even slowing them down a little will negatively affect their profits and we should do it more often. The maturity curve restarts when new technologies are introduced, such as mobile payments. This full curve can mature much faster in cyber businesses than in traditional business.
In contrast to payment card fraud, ad fraud is currently in the growth phase.
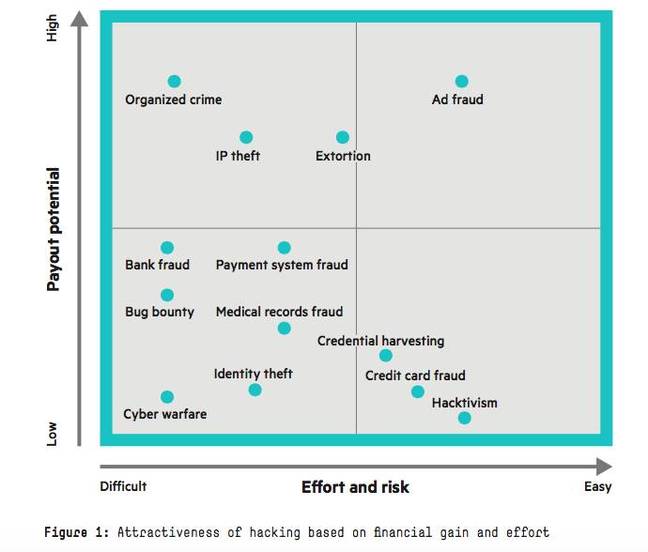
Cybercrime profit vs. effort chart (source: HPE report)
HPE’s study goes on to look at the organisational structure of criminal enterprises, concluding that they most often operate like "an eBay for illicit skills" - where reputation is paramount and individual sellers (or contractors) are the norm, in contrast to the more common general perception of hacking crews and Mafia-style activity.
These businesses do not operate in a hierarchy like a traditional enterprise but function more like a market‐driven fair economy of buyers and sellers, each of which works as an independent contractor providing value to the community. These contractors can choose their working hours and often work a separate job to supplement their activities.The underground cybercrime community is built on anonymity, and this anonymity can actually provide a radically free market system. The actors are only known by their handles and their true identities remain hidden. This breeds a strong paranoia throughout the business. Trust and a good reputation are key to the industry. If you are not trusted, it is very difficult to make money in the system. Trust is built by demonstrating your hacking skills, having other members of the community vouch for you, and providing valuable goods to the community. Groups often form around a shared common language (Russian, Chinese, etc.) or through gaming connections.
HPE’s research draws on data and observations from HPE’s security teams, open source intelligence and other industry reports. The study concludes with advice to security professionals and business leaders on strategies to disrupt the business of for-profit hacking.
“The business of hacking is a business just like ours. If we think of it like a business, like a competitor, then we can prioritize the most effective efforts to disrupt it,” HPE concludes. “All enterprise security technologies are intended to slow attackers in some way, with varying degrees of effectiveness. Some are effective at deterring opportunistic attackers (patching) but are ineffective at targeted attackers. Others are successful at reducing attacks of one type (EMV chip and pin credit cards), but lead attackers to move to alternate attack vectors (mobile payments).
“It is our duty as a legitimate enterprise to introduce these technologies to disrupt the business of hacking on a continuous basis. It is critical that an enterprise determine which technologies will be most effective at disrupting the adversaries targeting their unique business,” it adds. ®
