This article is more than 1 year old
Gamers! Ransomware will scramble your save files unless you cough up $1,000
Actually, it's about ethics in data kidnapping
Researchers have spotted malware that targets gamers, and threatens to trash their in-game progress unless they pay up.
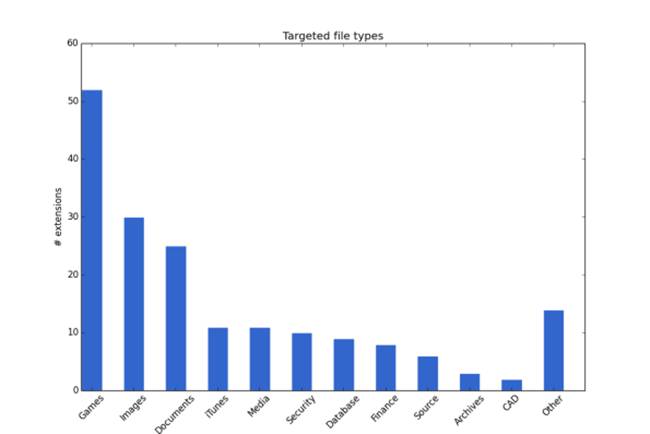
Of the 185 file types encrypted, games are Teslacrypt's top target
The software nasty, dubbed Teslacrypt, works in the same way as traditional ransomware like Cryptolocker. It attempts to infect Windows PCs by exploiting a vulnerability in Adobe Flash (CVE-2015-0311) or Internet Explorer (CVE-2013-2551). A victim has to visit a booby-trapped website to get infected, although the malware backs off if it detects the presence of some antivirus packages, or if it's running in a virtual machine.
Once installed, Teslacrypt scans the machine's file system, and encrypts files that match a list of types, generating a random AES key for each file using OpenSSL code and using that key to scramble the data. It then encrypts the AES keys using the public key from a 2048-bit RSA key pair.
The private key, needed to decrypt the per-file keys and ultimately restore the scrambled data, is stored on the criminals' command-and-control server.
Victims have to pay a ransom of $500 in Bitcoin, or buy and hand over a $1,000 Paypal My Cash payment card, using a website hidden in the Tor network, to download their decryption key before it is destroyed.
The command-and-control servers are hidden in the Tor network, and the malware communicates with these systems over HTTP. Teslacrypt also leaves the following files on infected machines...
%AppData%\<random>.exe %AppData%\key.dat %AppData%\log.html %Desktop%\CryptoLocker.lnk %Desktop%\HELP_TO_DECRYPT_YOUR_FILES.bmp %Desktop%\HELP_TO_DECRYPT_YOUR_FILES.txt
...and kills off any attempt to run these programs:
taskmgr procexp regedit msconfig cmd.exe
An analysis by Bromium Labs shows that under the skin TeslaCrypt is very different to Cryptolocker, sharing only eight per cent of executable code. And if it is using RSA cryptography, it seems the key pair is generated on the crims' systems.
The new malware also doesn't just focus on documents or images, but encrypts files associated with more than 20 games and gaming services – from user profile data to saved games, maps, and mods.
These include Call of Duty, World of Warcraft, Assassin's Creed, League of Legends, and Minecraft. In addition, it locks out Steam accounts, and developer tools like Unity3D and Unreal Engine.
"Encrypting all these games demonstrates the evolution of crypto-ransomware as cybercriminal target new niches," said Vadim Kotov, senior security researcher at Bromium.
"Many young adults may not have any crucial documents or source code on their machine (even photographs are usually stored at Tumblr or Facebook), but surely most of them have a Steam account with a few games and an iTunes account full of music. Non gamers are also likely to be frustrated by these attacks if they lose their their personal data."
And lose it they will. Despite analyzing the code, Bromium reports that breaking the encryption hasn't been managed yet, so those infected have little choice but to pay up, restore from offline backups (if they have been able to make them), or start their games all over again. ®
