This article is more than 1 year old
Received surprise new Redmond licenses? You might be pwned
Sleeping beauty rears ugly head
Black hats are flinging supposedly free licenses at enterprises in a bid to get malware on corporate networks, security bod Martin Nystrom says.
They wrote malware that was slightly neurotic in its bid to evade detection and would make use of the Tor network to receive stolen data.
The Cisco threat defence man said realistic phishing emails claiming approval for Microsoft licenses were personally-addressed to some of its customers foisting a link to where the malware would be downloaded.
He said the malware would search for sandboxes, a tool common with researchers, and put itself to sleep for up to half an hour to avoid detection.
"The email is very similar to the real email Microsoft sends," Nystrom said, adding analysis of the malware required a good measure of skill and resources.
"The malware seemed to know it was being analysed (by Nystrom) and exited after 20 seconds without doing anything.
"[It] sleeps to wait out automatic sandbox analysis before starting to communicate on the internet."
Attackers served a copycat Microsoft Volume Licensing Service Center page hosted on hacked WordPress sites where a low-detection Chanitor malware variant would quietly download seemingly as a volume license.
Once on a victim machine it would detect at least the three most popular sandboxes and use a sleep command to remain dormant for about 30 minutes.
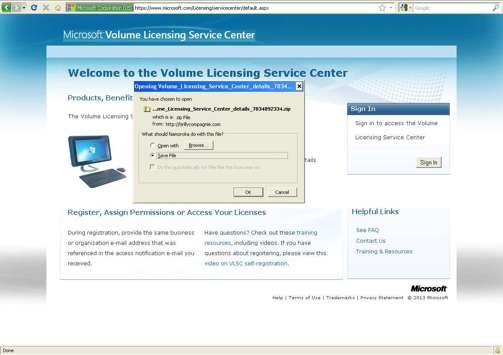
The fake site dropping malware
It would later alter a file structure to make some sandbox systems fail.
Chanitor also probed a series of IP addresses before checking if Tor network connections were possible.
Nystrom said the attack was typical of a trend to target corporate staff with smarter phishing emails, and of the continued cat-and-mouse game between white hat probing and black hat evasion. ®
