This article is more than 1 year old
Silver-tongued phish bait lures execs, hooks M&A deals
Swindlers savvy with corporate comms
A hacking group has been stealing identity information and reading emails to get the inside edge on stock markets to buy and sell to make quick profits.
Vendor FireEye reckons the group sent articulate phishing emails with malicious attachments demonstrating "deep" knowledge of financial markets and corporate communications.
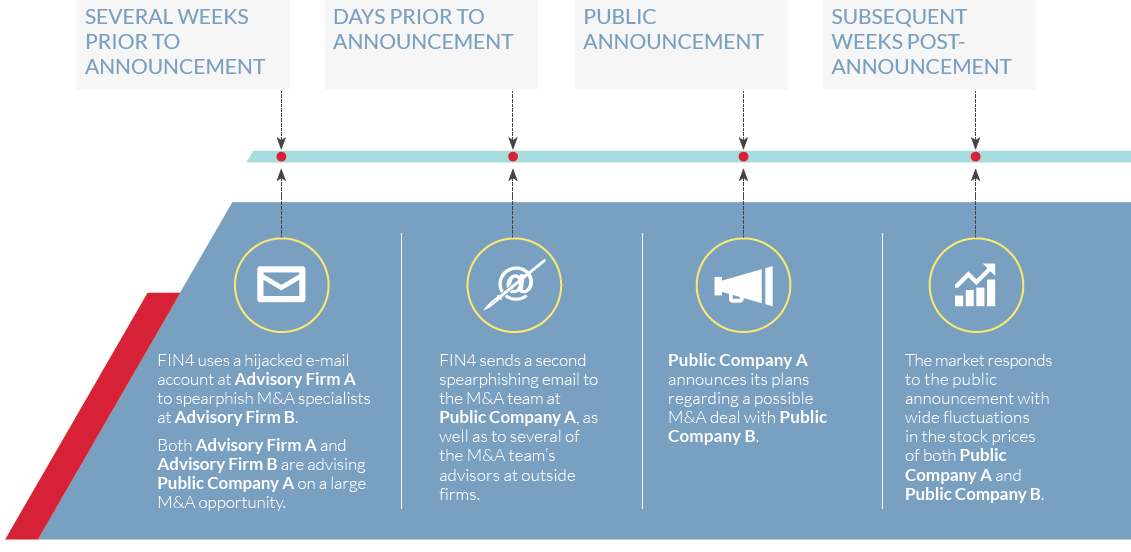
In one instance the attackers targeted five organisations involved in a then non-public merger, months before the deal was announced. In another, it used information gleaned from a hacked consultancy to better target that firm's clients.
Malware researchers Barry Vengerik; Kristen Dennesen; Jordan Berry, and Jonathan Wrolstad said the FIN4 group targeted 100 law, health care and pharmaceutical firms along with constancies including top executives over the last 18 months of which 98 were listed on the New York Stock Exchange or the NASDAQ.
"FIN4 knows their audience: Their spear phishing themes appear to be written by native English speakers familiar with both investment terminology and the inner workings of public companies," the quartet wrote in the report Hacking the Street? FIN4 Likely Playing the Market.
"... access to insider information that could make or break stock prices for dozens of publicly traded companies could surely put FIN4 at a considerable trading advantage.
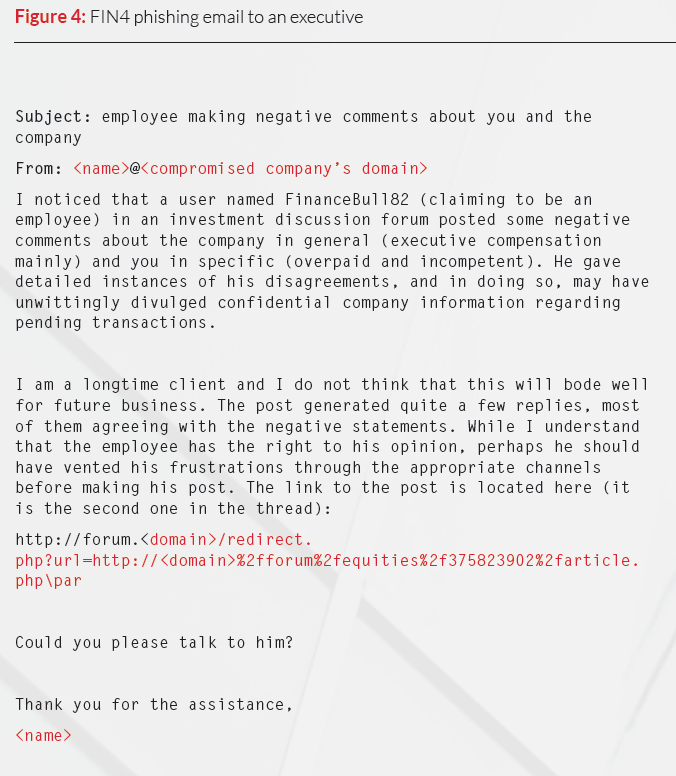
"Many of FIN4's lures appeared to be stolen documents from actual deal discussions that the group then weaponised (infected with malware) and sent to individuals directly involved in the deal."
Researchers discovered FIN4 after it targeted FireEye clients but had not found direct evidence the financial information was used to win on stock markets.
There was plenty of chance for ripe pickings, however. One hack was proceeded by a public acquisition in which stock prices were shaken in what the researchers said was an opportunity FIN4 "likely" capitalised on.
Moreover, FIN4's victims were individuals "privy to the most confidential information" of the listed companies who had secret information about merger and acquisition deals and "major market-moving announcements"
Attackers frequently employs M&A-themed and SEC-themed lures with Visual Basic for Applications macros implemented to steal the usernames and passwords of these key individuals."
FIN4 proved adaptable being able to respond quickly to news of clinical trials, regulatory decisions, and legal issues, researchers said, and had targeted staff involved in US Medicaid rebates and government purchasing presumably to gain insight into an organisation's future revenue.
"We've observed FIN4 access information on a wide variety of issues -- including drug development, insurance reimbursement rates, and pending legal cases -- all of which can significantly influence the price of health care industry stocks."
Phishing emails included malware-laced visual basic attachments that mimicked Windows email logins or links to fake web-based Outlook login pages.
The attackers even added email filter rules deleting mail with the words 'phish', 'malware' and 'hacked' in an apparent bid to crush warnings sent to victims.
Stolen data was tunnelled off to command and control servers over Tor and was sorted by keywords including 'CEO','SCIENTISTS_AND_RESEARCH' and organisation name. ®